Some college students are apparently willing to pay hundreds to off load a test or thousands for the whole course. Google “pay to do my homework” is the top monthly search phrase for the top sites most visited to rid one’s self of the onerous task of doing one’s own course work and to guarantee a good grade or your money back. The phrase, “Do my chemistry homework,” is another top favorite for those who would rather pay than study.
In 2014 when I first searched there were only a few companies in the business of taking student’s tests, but the field of competitors has grown. I was the Dean of Academic Technology for Colorado Community College Online (CCCO) then and was looking for a solution to making assessments secure. Faculty and administrators suspected that there was cheating going on, but we weren’t sure. We didn’t really know how much it was.
Talk about making the user’s experience effortless, it is so simple to do. Go to one of the company’s websites. Fill out the form. What test do you want taken? What is the URL of the test site, like your college’s login for the Learning Management System? Give them the login credential, password, and an email to contact you. A few minutes later, you get an estimate on what it will cost. Once you make your credit card payment, you are all set to get a good grade.
Of course, it is unethical and a violation of student conduct at all colleges, universities, and high schools to either share your login and password or let anyone else do your work. But, it is not easy to detect, and many, many are never caught. In 2015 we used tools that Biometric Signature ID (BSI) provided, along with some institutional data to uncover 58 students in only eleven courses that we suspected of sharing login credentials with another person, presumably for the purpose of cheating. An internal process was setup at our institution to develop a fast-track due process around the issue of sharing logins. CCCO provides community college level courses and because of the transient nature of our student body, we could not be sure they would be there the next term. It was therefore important to act as methodically and quickly as possible. As it turned out, some students were actually in a four-year college elsewhere but were using our online courses to finish a requirement that they would then transfer to their college. There is nothing wrong with this as students often use online courses to fit into their schedule courses they can’t always get at a time they need it or to try to catch-up on their credits. However, some of these students were also using another person to help them in their course. Briefly,
Here are the steps we developed in our process:
- RTEN’s (Real-Time Event Notifications) These are initiated by specific activities and situations by the student and detected by an algorithm setup for that purpose. An email notification is sent to the college representative for further action.
- Review the notification and determine if further research or action is necessary. Sometime an IP timing issue will be noted, which is the golden indicator of credential sharing.
- If reasonable suspicion is ascertained, the information found is sent to student services for a decision and possible action
- Student services may decide to wait and observe more or may decide to send a warning email to the student. This email is fashioned in such a way that it conveys our concerns about the security of the login credentials without accusations.
- Follow-up on a student’s login activities after a couple of weeks to determine if the suspected actions have stopped.
- If necessary, a second and possibly third letter of warning is sent out with some increasingly more direct language.
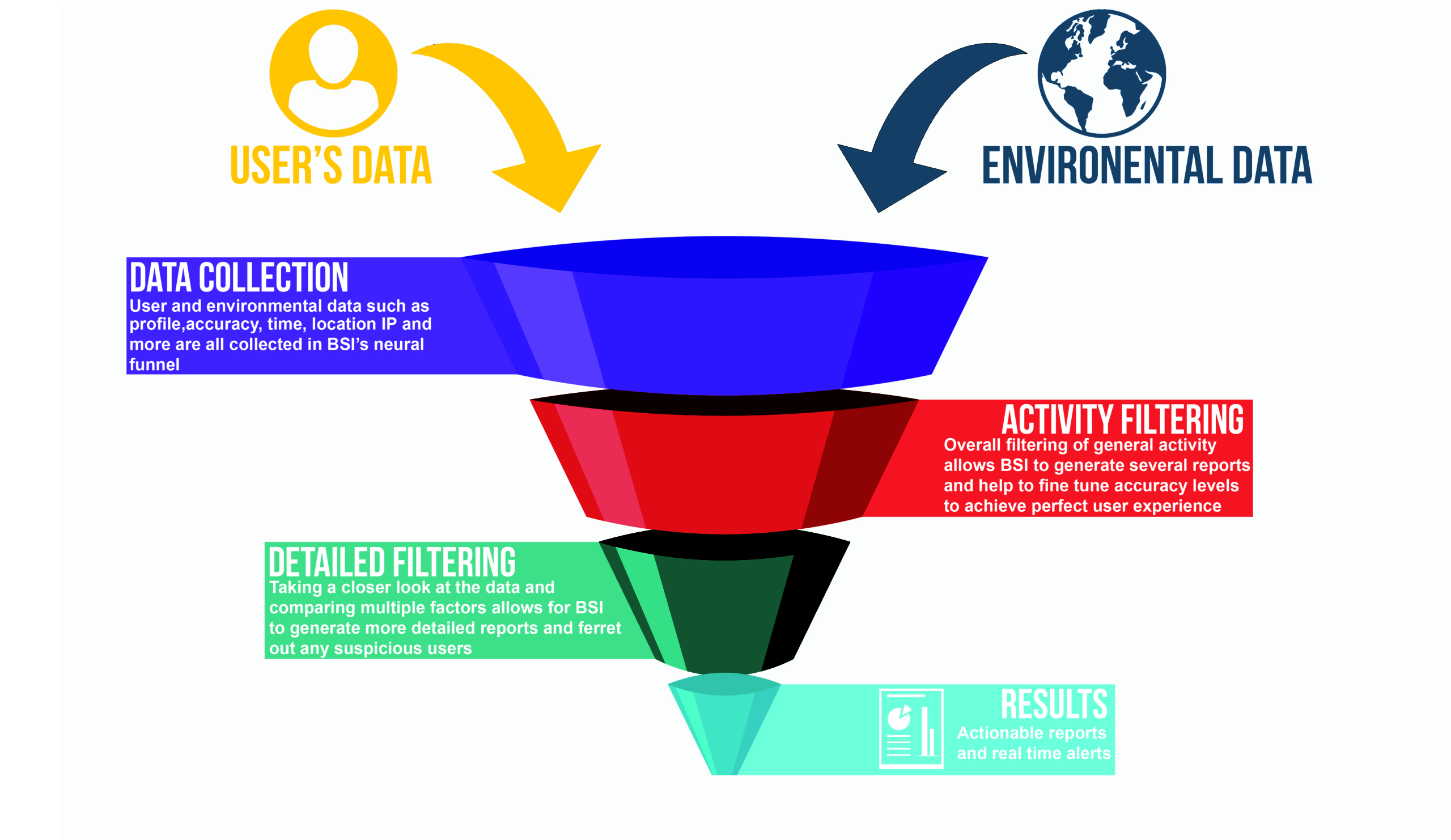
There has been much discussion and research in higher education around big data. For about two years I worked in a WCET project with a cross-section of large universities, private colleges, community colleges and mid-sized colleges to federate data for the specific purpose of trying to find any key factors in student success in college. It is a big project and it is not easy to do. Which is why I have been impressed with BSI’s ability to analyze the data in a way to provide pointers to where there may be some suspicious activity.
BSI clients who are using the RTEN service can do their own work, but not all colleges or universities have the FTE or training to pursue this type of investigation during the academic term. An alternate to DIY is the BSI Managed Services, where we can provide this service completely or any part of it. It is priced reasonably. If it is a small problem, then it doesn’t take long to clean it up. If it is larger, then it does take more time, but having the knowledge that you know where you are is important. No one wants to be an easy target to students bent on a short cut to a degree or the organizations that for money will do the course work.
In my experience the students who were warned the first time, ceased their erroneous activities immediately. Some chose to drop the course and a small number continued until they failed the course. However, no one disputed any of the warnings or the failed grades. How often does that happen? Verdict? Guilty!

Guest author, David Chatham, Former Dean of Academic Technology at Colorado Community Colleges Online – Now Director of Managed Services at BSI! Our top cop!
Contact us or schedule a web demo today!